Best practices for security with Modelbit
Modelbit provides various features and configuration options that relate to your security and data privacy. These are best practices for hardening the security of your Modelbit workspace.
API keys
API Keys are located in the Settings section of Modelbit. Click "API Keys" in the left-hand navigation.
When planning your API keys, consider when you may need to revoke them. Best practices are to have one API key per data scientist who may do testing, plus one API key per production environment that will call REST APIs, e.g. your web server.
Make sure to enable "Deployments Require API Keys."
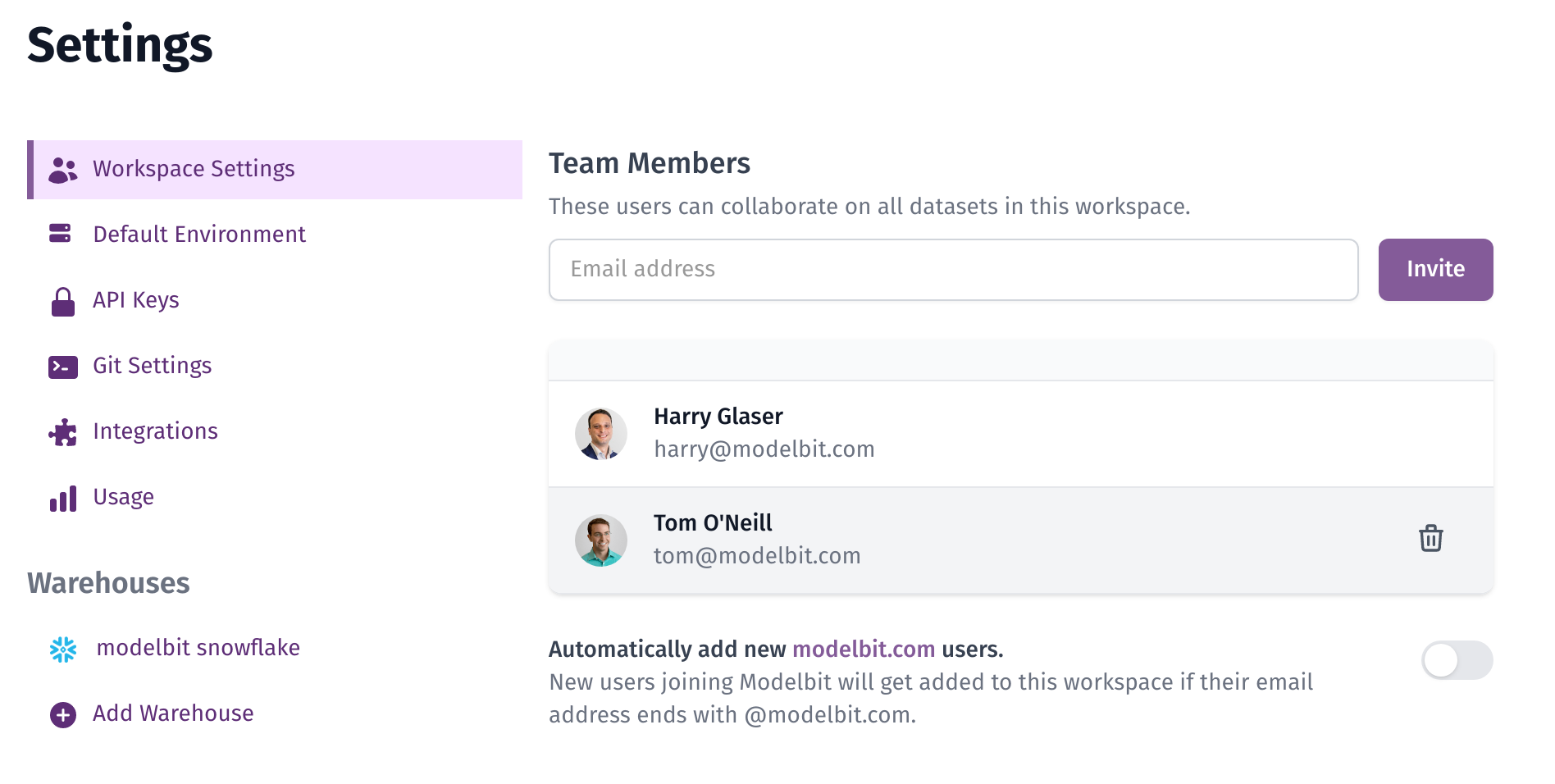
New users by invite only
Under "Workspace Settings" in Settings, make sure that "Automatically add new your_domain.com users" remains unchecked. This will ensure that only invited users have access to your corporate Modelbit workspace. Unauthorized employees who create accounts on the Modelbit website will be provisioned a demo workspace with no corporate access or privileges.
Data warehouse user role
Create a separate database role and user for Modelbit. Modelbit only requires the following permissions:
create role modelbit_role;
grant usage on warehouse <YOUR WAREHOUSE> to role modelbit_role;
grant usage on database <YOUR DATABASE> to role modelbit_role;
grant usage on schema <YOUR SCHEMA> ro role modelbit_role;
grant select on table <YOUR TABLE> to role modelbit_role; -- repeat as necessary for multiple tables
grant role modelbit_role to user modelbit_user;
create user modelbit_user default_warehouse = '<YOUR WAREHOUSE>' default_role = modelbit_role password='<MAKE A PASSWORD>';
Periodic reviews
Many security-conscious companies do periodic access reviews, e.g. quarterly. Make sure to check the following sections of Modelbit:
Periodic access reviews
Check these items to ensure your Modelbit security remains hardened:
- Workspace Settings: The users list should only contain active employees. As this list comes from SSO, if it contains a terminated employee, double-check your employee offboarding process with your SSO provider.
- API Keys: Only active team members and production environments should have API keys.
- Git Settings: Ensure that only active devices from your Mobile Device Management have their SSH keys in Modelbit.
- User Access Logs: Customers on Modelbit's Enterprise Plan may wish to audit employee access and usage logs in their own SIEM systems. Customers may contact Modelbit to enable and configure this feature.
Periodic hygiene reviews
These items do not impact Modelbit's security, but best practice is to avoid sprawl of unnecessary assets in Modelbit:
- Usage: Check your Usage settings to ensure model access patterns meet your expectations. Consider removing models that are not receiving usage.
- Git Branches: Check the list of git branches and delete any that are no longer in use.